A mercenary agent in the universe of Nite Team 4 (Fan post.. information in this post is for the game only)
This post is part of a series I wrote for the game Nite Team 4 - Military Hacking Division.
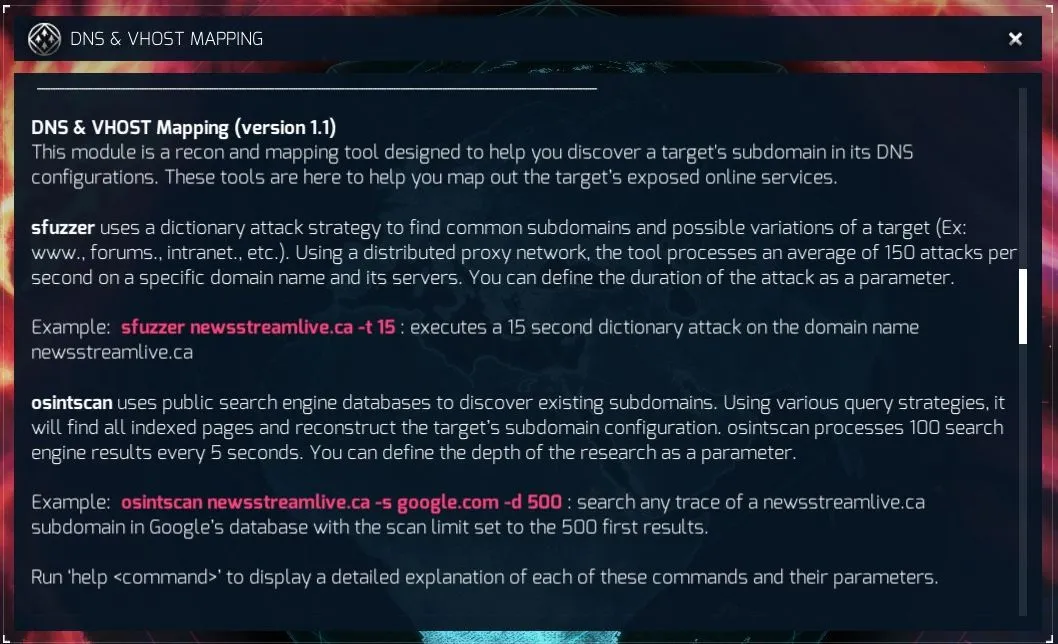
You’ve read all the help files right?
Before digging into the sfuzzer and osintscan commands, let’s review a few concepts. To start you need to understand what DNS and VHost are along with what domains, subdomains, and IPs. If you already know this, you can skip ahead, but I would rather educate than assume anything. You know what they say.
Domain Example: niteteam4.com Subdomain Example: factbook.niteteam4.com IP Example: 208.67.222.222
DNS
A long time ago, probably before some of you were born (man I feel old), to visit a server you had to know the IP address. The 4 octets combined gave you the address for that specific server. One of the most well known IP addresses is 127.0.0.1, which is a very special loopback address for your device. Also known as “home” and “localhost” it explains the humour behind “There’s no place like 127.0.0.1”.
Some very smart people realised that it was almost impossible to remember all server addresses and thus created Domain Name Systems or DNS. This is a human understandable abstraction of the IP address that literally transformed the internet, as it was now easy to tell people to go to your special GeoCities website and see what you were up to. It’s why you don’t have to type in an IP in order to access niteteam4.com.
This was a brilliant short term solution in a lot of ways. I say short term because there are a very limited amount of IP addresses. In fact, the last block of IPv4 address vanished earlier this year. Granted, there are still IP blocks to use, but it’s a real issue. There was, however, a solution.
VHosts
VHosts are virtual hosting platforms. What this means is that it is possible to have multiple domain names on the same IP address, but the server looks at the domain name you requested and serves the content for that specific address. Whether bred by need or fear, VHost are exceptionally common today. In fact, if you’re visiting a website it’s probably using the domain to access a special IP which then decided what content to feed you. We won’t go into load balancers and DMZs, etc here. Just know that virtual hosting is quite popular.
What this means for you, dear agent, is it is possible for a company to have multiple domains on the same IP address. This is a fact I cannot stress enough.
DNS and VHost Mapping
Now, our glorious StingerOS has a fantastic tool for information gathering when it comes to learning about the online presence for a company, agency, and individual. As long as you have a domain, subdomain, or IP address you can find out if the domain is actually on a VHost, or if it has subdomains that you can explore to exploit.
sfuzzer is godly - use it
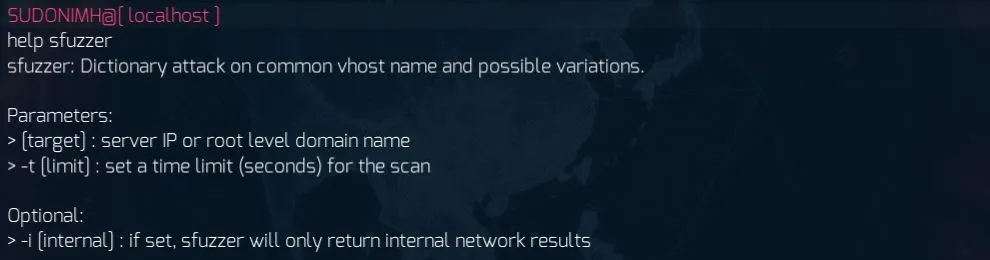
NOTE: you cannot use sfuzzer with IP addresses currently
This is one of my favourite tools. In fact it’s my go-to gadget when first investigating a domain. What this tool does is take the domain and uses a distributed proxy network to perform 150 dictionary-based attacks per second against the domain to see if there are any responses. If there are, they are reported to us.
*TIP: At this current moment in time, if sfuzzer doesn’t find something withing 2 minutes, it’s not going to find anything so a good time to run it at is 120. This gives you a glorious 18K attempts to find that subdomain!*
sfuzzer newsstreamlive.ca -t 120
*Bonus Tip: Do not hesitate to use sfuzzer with the -i switch once you’ve gained access to a network. This switch filters out external networks, which lets you hone in on what’s on the network you’re currently accessing.*
sfuzzer newsstreamlive.ca -t 120 -i
What does it mean by “dictionary attack strategy”? In the world today, it is common to try and use the name of a service for a domain as it’s subdomain. As an example www is actually a subdomain for displaying a website (html, etc). While you can have a website on a subdomain other than www, it’s pretty common practice to use it.
Another example of a subdomain is mx.domainname.com. MX stands for Mail Exchange. This is what is used to tell your email to go to the right place.
Other common subdomains include, but are obviously not limited to, ftp, smtp, pop, imap, vpn, and adserver.
OSINTSCAN - This is a beast!
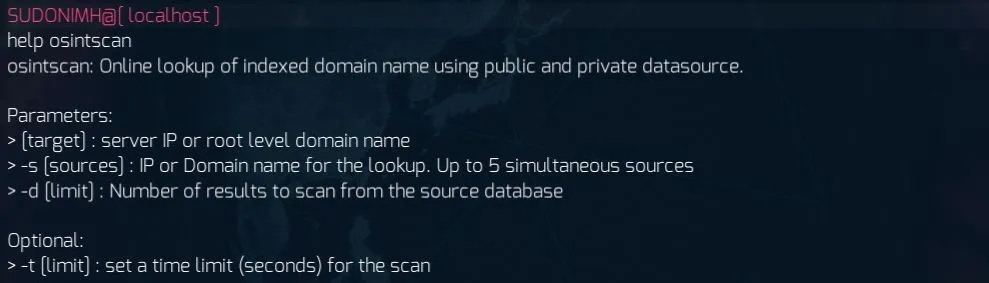
Note: At this current moment in time, you cannot set a time limit on osintscan
This tool can also find subdomains like sfuzzer, but what makes this stand out is it can actually help you figure out if a domain is on a vhost. This makes the tool absolutely invaluable. Sometimes the results will reveal more than just the subdomains, it will reveal to you the IP address the server is on.
If that happens, and I cannot stress this enough, be sure you do some scanning on that IP address as well as you may find other subdomains or even domains on that server. Knowledge is power agents!
*TIP: There are four key search engines you can use to gain information about a target: google.com, bing.com, yahoo.com, and tbw.com. Gotta love The Black Watchmen for being so helpful!*
*Bonus Tip: You can actually search each engine in the same command!*
osintscan newsstreamlive.ca -s google.com bing.com yahoo.com tbw.com -d 500
*Super Bonus Tip (thanks Agent DJF1107): If you’re wanting to focus on finding an IP address… use bing.*
Sometimes, no matter how hard you try, every subdomain you examine to find a vulnerability may be completely up to date with no known vectors for attack. It is at that time you need to seriously consider looking into the Social Engineering Toolkit (or SET), but that is for another tutorial.
Good luck agents, you’re going to need it. Till next time…
Special thank you to Agent Tibleam, Agent Pherret, and Agent DJF1107 for verifying and catching a few things I missed.
